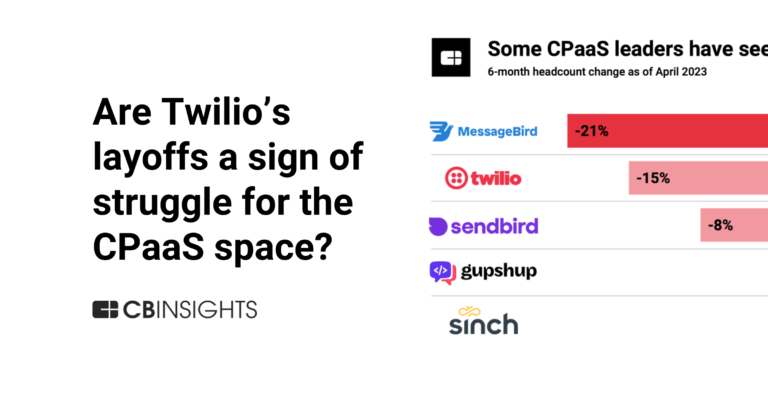
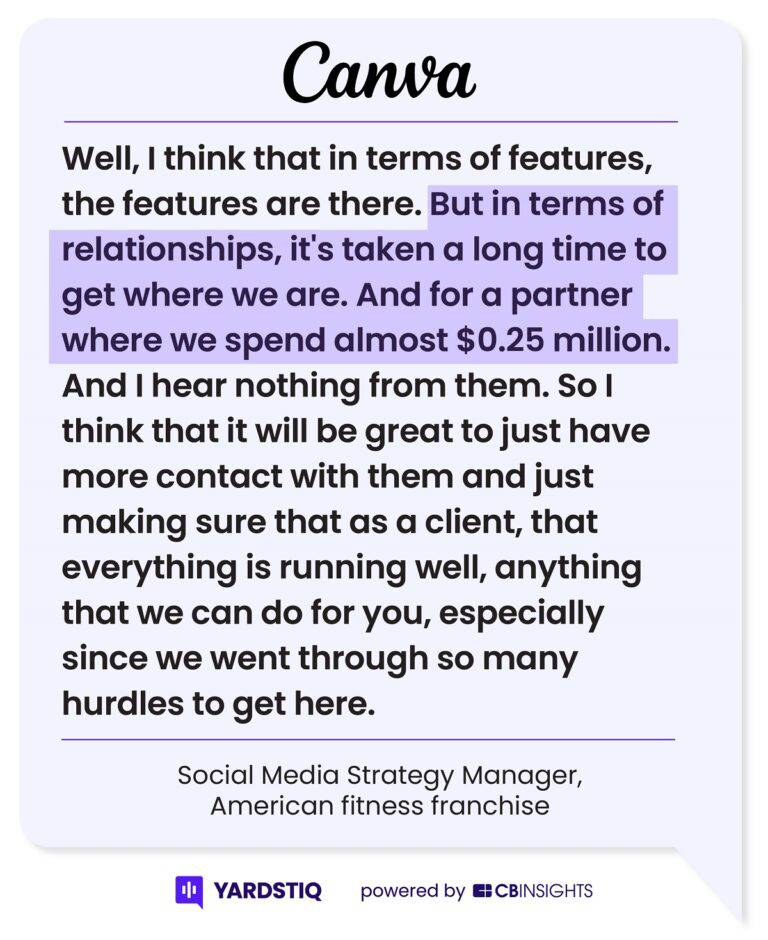
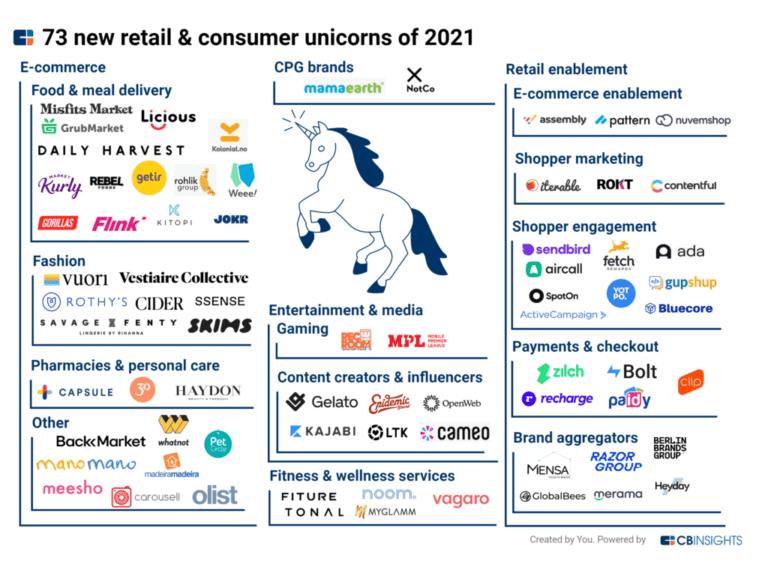
Sendbird
Founded Year
2013Stage
Series C | AliveTotal Raised
$219.64MValuation
$0000Last Raised
$100M | 4 yrs agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
-31 points in the past 30 days
About Sendbird
Sendbird focuses on providing in-application communication solutions, operating within the technology and communications industry. The company offers a platform that enables businesses to integrate chat, voice, video, and live stream capabilities into their applications, enhancing customer engagement and retention. Sendbird primarily serves sectors such as financial services, digital health, marketplaces, on-demand services, retail and travel, and social communities. It was founded in 2013 and is based in San Mateo, California.
Loading...
ESPs containing Sendbird
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The digital adoption platforms market is a fast-growing space that offers businesses a solution to streamline the adoption and usage of digital tools and applications. These platforms provide interactive guidance and training to end-users, allowing them to quickly and effectively learn how to use new software, reducing frustration and improving productivity. They can also help businesses reduce tr…
Sendbird named as Challenger among 15 other companies, including Oracle, WalkMe, and WhatFix.
Loading...
Research containing Sendbird
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Sendbird in 7 CB Insights research briefs, most recently on May 17, 2023.
Nov 28, 2022
The Transcript from Yardstiq: Feel the churn
Oct 26, 2022 report
Top omnichannel communications companies — and why customers chose them
Oct 11, 2022
The Transcript from Yardstiq: Klarna vs. Afterpay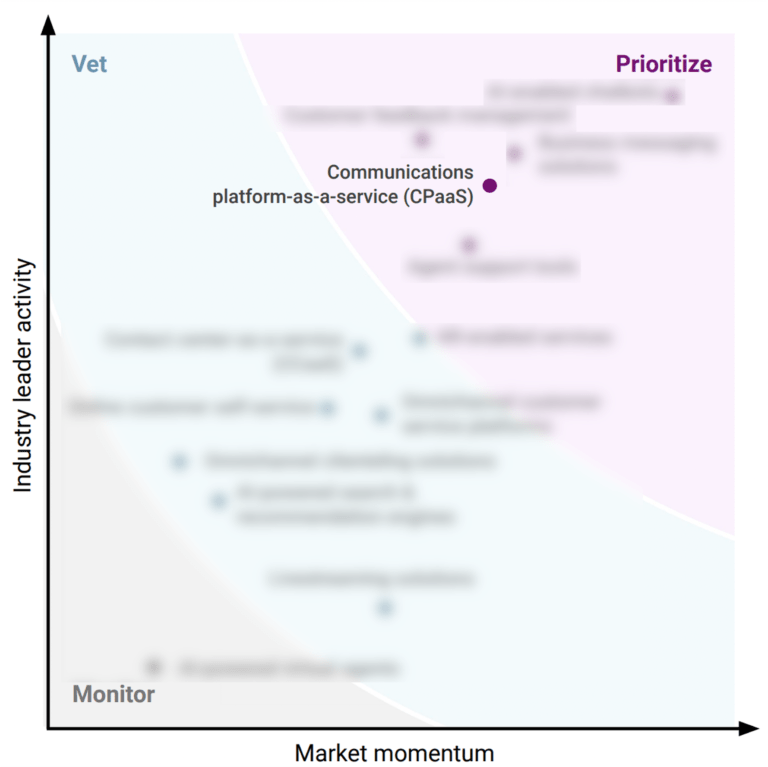
Expert Collections containing Sendbird
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Sendbird is included in 3 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,257 items
Future Unicorns 2019
50 items
Sales & Customer Service Tech
1,058 items
Companies offering technology-driven solutions for brands and retailers to enable customer service before, during, and after in-store and online shopping.
Latest Sendbird News
Dec 10, 2024
Cybersecurity jobs available right now: December 10, 2024 Cloud Security Engineer As a Cloud Security Engineer, you will work with engineering teams to build secure infrastructure at scale, secure multi-account and multi-cloud infrastructure for Sendbird, own CSPM and cloud security tooling while building automations, embed security tools into the CI/CD system for IaC scanning, identify security gaps and develop solutions, and research and identify new attacks targeting Sendbird’s products. Cyber Network Analyst As a Cyber Network Analyst, you will conduct cyber security investigations in medical networks using Cynerio’s solutions. Identify and analyze potential security incidents that currently exist or may pose a potential threat to customer networks. Conduct blackbox network analysis of proprietary or obscure protocols used by medical and IoT devices. Cyber Security Architect As a Cyber Security Architect, you will lead security risk assessments and vulnerability analyses for SaaS platforms, IoT devices and associated software and firmware. Design and implement security controls and countermeasures to protect IoT products from threats. I have read and agree to the terms & conditions Leave this field empty if you're human: Cyber Threat Specialist, Threat hunting As a Cyber Threat Specialist, Threat hunting, you will prevent, detect and respond to Threat Intelligence to reduce cyber risk at AXA XL. Apply knowledge of current and past malware methods, attack methodologies, and TTPs to discover anomalies and trends within data. Lead investigations using multiple data/intelligence sources and tools to track down and detect cyber threat actors and activity that may have breached company’s defenses. Data Protection Specialist As a Data Protection Specialist, you will develop and maintain data protection procedures and standards to align with regulatory requirements and security strategies. Continuously monitor and assess data protection risks and data protection metrics. Conduct RoPA assessments and ensure timely delivery of identified deviations. Deputy CISO As a Deputy CISO, you will lead annual NIST CSF maturity assessments and drive continuous improvement initiatives. Develop and maintain security policies, standards, and procedures. Lead incident response activities, including investigation, containment, eradication, and recovery. DevOps Security Engineer with DLP As a DevOps Security Engineer with DLP, you will automate on-prem infrastructure processes to implement and enhance DLP controls, improve DevOps practices within the squad by leveraging Infrastructure as Code, test automation, and CI/CD, and manage a global DLP security infrastructure while working with various security products such as Symantec DLP, Splunk, Microsoft Information Protection, and Netskope. Embedded Security Engineer As an Embedded Security Engineer, you will be responsible for conducting comprehensive threat modeling and security assessments, as well as supporting our engineering teams in adhering to established security standards and requirements. Head of Cyber Security Architecture As a Head of Cyber Security Architecture, you will develop and implement the overall cyber security architecture strategy. Develop and actively drive the implementation of cyber security architecture and capabilities, through continues improvements, projects as well as through large business transformation programs. Align security initiatives with business goals and regulatory requirements. Information Security Manager As an Information Security Manager, you will oversee and directly manage the maintenance and optimization of IT infrastructure, including networks, servers, and software applications. Develop and implement security policies and protocols, performing hands-on tasks to protect company data and systems from cyber threats. InfoSec Program Manager As an InfoSec Program Manager, you will develop, maintain, and enhance the organization’s security program. Identify, assess, and mitigate security risks across the technology stack. Lead incident response efforts, including investigation, containment, and recovery. Intern – Penetration Testing / Ethical Hacking As an Intern – Penetration Testing / Ethical Hacking, you will help conduct vulnerability scans and penetration testing using industry tools. Assist in web app testing aligned with OWASP (Open Web Application Security Project) standards. With guidance, learn to simulate real-world attacks to assess system security. IT Security Engineer As an IT Security Engineer, you will perform risk assessment analysis, by identifying vulnerabilities that could be exploited by malicious attackers, to proactively anticipate and prevent cyber-attacks. Develop security protocols, standards and policies, as well as disaster recovery plans and conducting security audits. Network Security Specialist As a Network Security Specialist, you will configure, manage, and maintain various firewalls and security solutions, including but not limited to F5, Cisco, Palo Alto, Check Point, and other platforms. Manage and optimize cloud environments, ensuring high availability and security. Support and troubleshoot Linux-based operating systems and ensure their stability and security. OT Information Security Specialist As an OT Information Security Specialist, you will be responsible for documenting and updating, as appropriate the information security policy, standards and processes ensuring these are communicated and actively considered during solution and service design. Monitoring, auditing and reporting on compliance to IT security standards: highlighting compliance breaches or potential risks. Principal Cloud Threat Intelligence Researcher (Cortex) As a Principal Cloud Threat Intelligence Researcher (Cortex), you will hunt and track cloud threat actors as they perform their operations. Add insight into cloud threat actors and enrich indicators from cloud environments. Build Cortex detection coverages for cloud vulnerabilities, exploits, and malware. Security Applications Engineer As a Security Applications Engineer, you will establish and maintain DLP policies to prevent unauthorized access, transmission, or disclosure of sensitive data, focusing on both on-premises and cloud environments. Design, implement, and manage CASB solutions to control and monitor access to cloud applications and safeguard data across cloud services. (Senior) Data Privacy Specialist As a (Senior) Data Privacy Specialist, you will conduct risk assessments, define and track implementation of requirements for technical data privacy compliance for Global Connected Car Systems on vehicle level and cloud environment with focus EU/UK, EMEA, APAC, USA (Privacy by Design). Senior Network Security Architect As a Senior Network Security Architect, you will lead the design and implementation of network security architectures, ensuring they meet regulatory standards and strategic objectives. Develop network segmentation strategies to align with PCI DSS and other industry regulations, minimizing risk and enhancing security. Senior Penetration Tester As a Senior Penetration Tester, you will perform in-depth penetration tests across applications, infrastructure, cloud and mobile platforms. Execute zero-knowledge black-box, grey-box and white-box penetration tests of specific areas within the enterprise. Perform tests and assessments in the cloud, including but not limited to AWS, Azure, GCP, etc. Specialist, Network Security As a Specialist, Network Security, you will design, implement, and maintain enterprise network-security infrastructure and multi-cloud platforms, including firewalls, wireless systems, and load balancers. Conduct regular network and security audits to identify vulnerabilities and recommend appropriate remediation measures. More about
Sendbird Frequently Asked Questions (FAQ)
When was Sendbird founded?
Sendbird was founded in 2013.
Where is Sendbird's headquarters?
Sendbird's headquarters is located at 400 1st Avenue, San Mateo.
What is Sendbird's latest funding round?
Sendbird's latest funding round is Series C.
How much did Sendbird raise?
Sendbird raised a total of $219.64M.
Who are the investors of Sendbird?
Investors of Sendbird include Tiger Global Management, ICONIQ Growth, SoftBank, Emergence Capital, WiL and 13 more.
Who are Sendbird's competitors?
Competitors of Sendbird include Social Plus, FreeD Group, RingOver, CometChat, SignalWire and 7 more.
Loading...
Compare Sendbird to Competitors

SignalWire is a company focused on cloud communications and programmable unified communications within the tech industry. Its main offerings include a suite of APIs for voice, messaging, and video, enabling developers to create and scale communication applications such as call centers and PBXs. SignalWire's services are designed to integrate and provide low-code solutions for various sectors including contact centers, education, and healthcare. It was founded in 2017 and is based in Palo Alto, California.

Plivo is a cloud communications platform that offers SMS and voice API solutions. The company provides APIs that allow businesses to send and receive text messages, integrate voice calling into applications, and engage customers across various channels. Plivo's services are used by sectors such as healthcare, finance, hospitality, retail, and government. It was founded in 2011 and is based in Austin, Texas.

Telnyx specializes in providing global solutions for communications, the Internet of Things (IoT), artificial intelligence (AI), and networking. It offers a suite of communication application programming interfaces (APIs), IoT device connectivity, and AI-powered applications, all underpinned by a global private network. Telnyx primarily serves sectors that require scalable and reliable cloud communication services, such as contact centers, patient monitoring systems, and marketing messaging platforms. It was founded in 2009 and is based in Chicago, Illinois.

Unifonic provides a customer engagement platform and operates in the communication and technology industry. The company offers a platform to integrate various communication channels, messaging apps, and chatbots to businesses for customer interactions and to build relationships. It primarily serves sectors such as banking and finance, government, healthcare, retail and electronic commerce, and transport and logistics. Unifonic was formerly known as Optimal Technology Solutions. It was founded in 2006 and is based in Riyadh, Saudi Arabia.

Stream specializes in providing scalable APIs and SDKs for real-time chat messaging, video and audio communications, and activity feeds across various applications. The company offers a suite of tools that enable developers to build and integrate rich conversational and community engagement features into their apps. Stream's products are designed to cater to sectors such as social media, gaming, healthcare, education, and more. It was founded in 2015 and is based in Boulder, Colorado.

eyeson is a provider of smart video collaboration solutions. The company's core product is a cloud-based software solution providing a video conferencing platform that aims to optimize collaboration. It is based on a patented real-time communication server with Single-Stream-Technology, providing video and audio quality regardless of the number of participants. eyeson is available for several online collaboration tools and developers can easily integrate eyeson's API into their own apps.
Loading...