Orca Security
Founded Year
2019Stage
Series C - II | AliveTotal Raised
$632MValuation
$0000Last Raised
$340M | 3 yrs agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
+61 points in the past 30 days
About Orca Security
Orca Security focuses on cloud security. It offers a cloud security platform that provides services such as identifying and remediating misconfigurations across clouds, protecting virtual machines, containers, and serverless functions, and monitoring and responding to threats across the cloud attack surface. The company primarily sells to sectors such as financial services, technology, government, retail, healthcare, and media & entertainment. It was founded in 2019 and is based in Portland, Oregon.
Loading...
Orca Security's Product Videos
ESPs containing Orca Security
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The vulnerability management market helps organizations identify and prioritize vulnerabilities in their IT systems, networks, and applications. Solutions aim to reduce the risk of cyberattacks and data breaches by providing insights into potential security gaps and offering guidance on how to remediate them. Some vendors offer benefits such as increasing IT productivity, providing threat intellig…
Orca Security named as Challenger among 15 other companies, including Palo Alto Networks, Tata Consultancy Services, and New Relic.
Orca Security's Products & Differentiators
Orca Cloud Security Platform
Orca Security is the industry-leading Cloud Security Platform that identifies, prioritizes, and remediates security risks and compliance issues across your cloud estate spanning AWS, Azure, Google Cloud and Kubernetes. Orca detects all of your cloud risks and prevents them from recurring in future. We’re differentiated to provide 100% frictionless coverage Comprehensive platform of capabilities to address misconfigurations, vulnerabilities, lateral movement, active infections, and more Risk prioritization avoids long lists of alerts to focus on vital attack paths across multiple risk categories
Loading...
Research containing Orca Security
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Orca Security in 8 CB Insights research briefs, most recently on Sep 6, 2023.

Sep 6, 2023
The data security market map
Aug 10, 2023
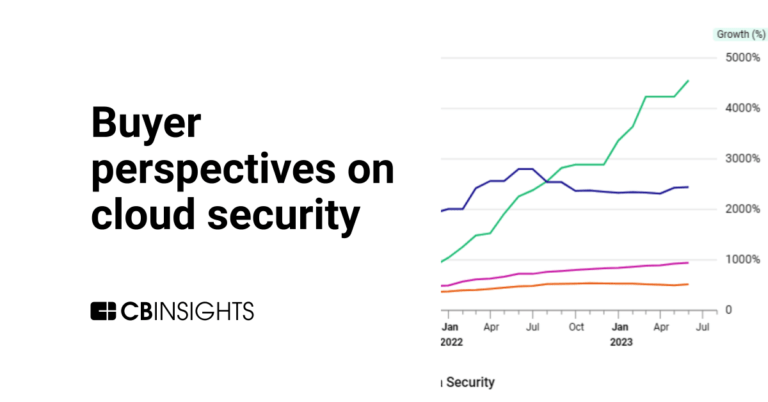
How much are CISOs spending for cloud security?
Jul 28, 2023
The cloud security market map

Oct 11, 2022
The Transcript from Yardstiq: Klarna vs. Afterpay
Oct 4, 2022
The Transcript from Yardstiq: Ramp vs. Brex
Sep 26, 2022 report
Top cloud security companies — and why customers chose themExpert Collections containing Orca Security
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Orca Security is included in 3 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,261 items
Regtech
1,611 items
Technology that addresses regulatory challenges and facilitates the delivery of compliance requirements. Regulatory technology helps companies and regulators address challenges ranging from compliance (e.g. AML/KYC) automation and improved risk management.
Cybersecurity
10,442 items
These companies protect organizations from digital threats.
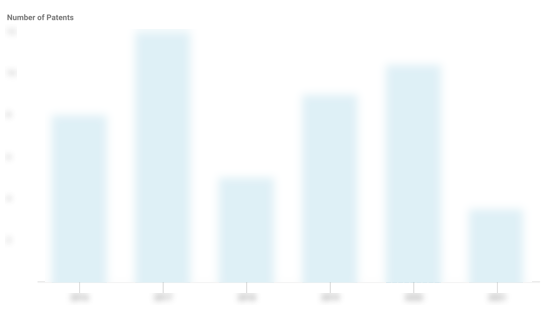
Orca Security Patents
Orca Security has filed 23 patents.
The 3 most popular patent topics include:
- cloud computing
- cloud infrastructure
- computer security
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
4/6/2022 | 3/26/2024 | Cloud infrastructure, Cloud computing, Computer security, Computer security exploits, Computer network security | Grant |
Application Date | 4/6/2022 |
|---|---|
Grant Date | 3/26/2024 |
Title | |
Related Topics | Cloud infrastructure, Cloud computing, Computer security, Computer security exploits, Computer network security |
Status | Grant |
Latest Orca Security News
Feb 22, 2025
With sophisticated threats and increasingly complex cloud environments, AI-based solutions provide organizations with the means to detect, prevent, and effectively respond to cyber risks. As Cyber News says, AI is revolutionizing cloud security by analyzing immense amounts of data, detecting anomalies, and automatically responding to them. This article gives a discussion on how AI transforms cloud security, with a focus on key advancements and what they mean for the future. The Role of AI in Cloud Securit The unique challenges that cloud environments present have received a good measure of solutions from AI, with perhaps some assistance from human beings. Traditional approaches to security start to fall short when confronted by the ever-changing conditions of the cloud, wherein workloads, users, and data flows are all subject to continuous change. AI can fill this strategic gap by providing real-time threat detection, prediction, and automated response. Cyber Security Newsrecently published another piece on its platform that made the claim that AI systems, while enhancing the accuracy of threat detection tremendously, were also simultaneously decreasing the time taken to respond to threats, thereby becoming some of the greatest enablers of cybersecurity strategies today. One of the greatest strengths is behavioral baselining of the users and systems, which AI establishes. The ongoing monitoring of activities over a cloud environment allows the AI to catch even the slightest deviation that would spell a malicious act. The Role of Cloud Penetration Testing Cloud penetration testing evaluates the security of cloud-hosted applications, databases, and infrastructure by replicating real-world attack scenarios. The goal is to identify vulnerabilities, assess risks, and recommend remediation strategies before malicious actors exploit them. This process not only strengthens an organization's security posture but also ensures compliance with industry standards and regulations. Penetration testing can take several forms: Black Box Testing: Simulating an external attack without prior knowledge of the cloud environment. White Box Testing: Conducting tests with full access to system architecture and configurations. Grey Box Testing: Combining elements of both black box and white box testing for a balanced approach. By testing all components of a cloud environment with some of the best penetration testing companies that offer authentication controls, APIs, virtual machines, and storage systems penetration testers provide organizations with actionable insights into their security gaps. Key Applications of AI in Cloud Security Automated Threat Intelligence: AI analyzes global data in real time to detect threats and predict vulnerabilities, enabling proactive defense. Anomaly Detection: AI compares activities against baselines to detect suspicious behavior, reducing false positives and enhancing security. Adaptive Access Controls: AI dynamically adjusts access based on user context, adding authentication steps for high-risk activities. Malware Detection: AI detects polymorphic malware by analyzing behavior, providing stronger protection than signature-based methods. Predictive Risk Management: AI forecasts risks and simulates attacks, helping organizations preemptively strengthen their defenses. Deception Technology: AI-powered decoys mimic real assets, diverting attackers and collecting intelligence on their tactics. Real-World Examples of AI in Action Several cutting-edge solutions demonstrate how AI is transforming cloud security: Dynatrace's Davis AI Engine: This platform uses machine learning to predict IT infrastructure failures and potential breaches before they occur. Its preventive approach ensures application reliability while accelerating incident resolution. Darktrace's Cyber AI Analyst: This tool autonomously analyzes alerts and triages incidents across multi-cloud environments. By correlating network activity with user behavior, it detects malicious actions with surgical precision. Orca Security's Anomaly Detection: Orca leverages machine learning algorithms to continuously monitor cloud workloads for deviations from baseline behavior, minimizing false positives while enabling rapid response. Challenges in Implementing AI-Driven Cloud Security While the benefits of AI in cloud security are undeniable, integrating these technologies into existing infrastructures comes with challenges: Data Privacy Concerns: The use of AI requires access to large datasets for training and analysis, raising concerns about data privacy and compliance with regulations like GDPR. Scalability Issues: As cloud environments grow more complex, ensuring that AI systems can scale effectively without compromising performance is critical. Cost Implications: Implementing advanced AI solutions can be expensive, particularly for small and medium-sized enterprises (SMEs). However, many providers now offer scalable options tailored to different budgets. Conclusion AI is now a greatly-needed weapon to stem cyber threats in cloud environments. AI, which automates threat detection, provides the means for better anomaly detection and predictive risk management, thereby ensuring that organizations can respond swiftly without causing much damage during a breach. A piece such as Cybersecurity News sheds some light on how companies use these technologies to enhance their security frameworks efficiently. According to Cyber Press, integrating AI in cloud security helps enhance accuracy and reduces response times to a large extent, both of which are critical in countering modern cyber threats. Some organizations face the issue of scalability and cost. Currently, advancements in AI seem quite hopeful for affordable ways to address different circumstantial needs. In an age of digital transformation where industries are freed to innovate, the acquisition of artificial intelligence is no longer an option for cloud security but an essential tool for protecting sensitive information and business continuity in an inherently interlinked world.
Orca Security Frequently Asked Questions (FAQ)
When was Orca Security founded?
Orca Security was founded in 2019.
Where is Orca Security's headquarters?
Orca Security's headquarters is located at 1455 North West Irving Street, Portland.
What is Orca Security's latest funding round?
Orca Security's latest funding round is Series C - II.
How much did Orca Security raise?
Orca Security raised a total of $632M.
Who are the investors of Orca Security?
Investors of Orca Security include Notable Capital, Redpoint Ventures, CapitalG, ICONIQ Capital, Stripes Group and 13 more.
Who are Orca Security's competitors?
Competitors of Orca Security include Edera, Solvo, Upwind, Wiz, Aqua Security and 7 more.
What products does Orca Security offer?
Orca Security's products include Orca Cloud Security Platform.
Who are Orca Security's customers?
Customers of Orca Security include Four Kites, Hunters, Postman, Lemonade and BeyondTrust.
Loading...
Compare Orca Security to Competitors

Wiz provides cloud security software within the cybersecurity industry. Its main offerings include a unified cloud security platform that enables security, development, and operations teams to collaborate and secure cloud environments effectively. Wiz's platform offers solutions for continuous security posture management (CSPM), container and Kubernetes security, cloud workload protection (CWPP), identity and access management (CIEM), and data security posture management (DSPM), among others. It was founded in 2020 and is based in New York, New York.

Sysdig provides security for cloud-based systems, containers, and Kubernetes. The company offers a platform that helps detect threats, manage vulnerabilities, control risks across multiple cloud environments, and manage permissions. It primarily serves the cloud computing industry. It facilitates vulnerability management, posture management, cloud monitoring, custom metrics, and more. Its products are Sysdig Platform and Sysdig Monitor. It was formerly known as Draios. It was founded in 2013 and is based in San Francisco, California.

Aqua Security specializes in cloud-native security. The company offers a comprehensive cloud-native application protection platform that provides prevention, detection, and response automation across the entire application lifecycle, securing the build, cloud infrastructure, and running workloads. It primarily serves sectors such as finance and the federal government. Aqua Security was formerly known as Scalock. It was founded in 2015 and is based in Burlington, Massachusetts.

Uptycs is a cloud security company that specializes in protecting hybrid cloud environments and providing visibility from development to runtime. The company offers a suite of security solutions, including workload protection, compliance automation, threat detection and response, and security for containers and Kubernetes. Uptycs serves enterprises by optimizing security operations, ensuring compliance, and accelerating remediation across cloud workloads, containers, Kubernetes, and software pipelines from a unified security console. It was founded in 2016 and is based in Waltham, Massachusetts.
CloudWize provides cloud security and compliance solutions across various domains. The company offers a platform for threat monitoring, misconfiguration detection, and compliance risk management for cloud environments. CloudWize serves sectors that require cloud security measures, such as the technology and cybersecurity industries. It was founded in 2019 and is based in Netanya, Israel.

Upwind provides cloud security in the technology sector. It offers services such as threat detection, vulnerability management, and cloud security posture management, all aimed at securing hosts, containers, virtual machines, and serverless functions. The company primarily serves the cloud computing industry. It was founded in 2022 and is based in San Francisco, California.
Loading...