
Huntress
Founded Year
2015Stage
Series D | AliveTotal Raised
$308.05MValuation
$0000Last Raised
$150M | 8 mos agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
+62 points in the past 30 days
About Huntress
Huntress provides a managed security platform that offers endpoint detection and response, antivirus protection, ransomware detection, and security awareness training. Huntress primarily serves small and mid-market businesses, IT service providers, and value-added resellers. It was founded in 2015 and is based in Ellicott City, Maryland.
Loading...
ESPs containing Huntress
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The security awareness training market helps organizations reduce human-caused security incidents through employee education platforms. Many solutions combine interactive training modules with practical tools such as phishing simulations and security assessments. Core focus areas include password security, phishing awareness, and data protection protocols.
Huntress named as Highflier among 15 other companies, including Arctic Wolf Networks, Proofpoint, and KnowBe4.
Loading...
Expert Collections containing Huntress
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Huntress is included in 2 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,258 items
Cybersecurity
10,080 items
These companies protect organizations from digital threats.
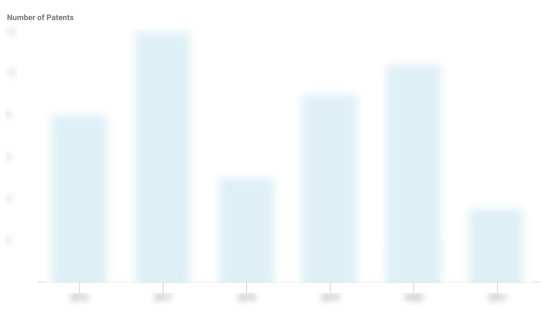
Huntress Patents
Huntress has filed 4 patents.
The 3 most popular patent topics include:
- computer network security
- computer security
- linux kernel features
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
5/24/2023 | 6/18/2024 | Computer network security, Computer security, Computer networking, Packets (information technology), Linux kernel features | Grant |
Application Date | 5/24/2023 |
|---|---|
Grant Date | 6/18/2024 |
Title | |
Related Topics | Computer network security, Computer security, Computer networking, Packets (information technology), Linux kernel features |
Status | Grant |
Latest Huntress News
Dec 14, 2024
Back in May, Microsoft jubilantly announced Recall, an AI feature for some Windows PCs that silently takes screenshots every five seconds and then allows you to easily search through the resulting digital footprint. Forgotten where you saw a recipe online? Tapping a couple of keywords into Recall could, in theory, find the dish again. It didn’t take long for the privacy and security community to find gaping holes in the feature . In response, Microsoft delayed Recall’s launch and eventually made some significant changes —such as making Recall opt-in rather than on by default, better encrypting information captured by Recall, and adding authentication to access data that it stored. Recall finally launched for some users this month. However, this week, testing of Recall by Tom’s Hardware demonstrated that a key safeguard put in place by Microsoft can still fail. With a Recall setting called “filter sensitive information” turned on, Tom’s Hardware’s tests found that it still took screenshots of some sensitive information—such as credit card numbers and Social Security numbers. When the publication typed a credit card number and a username and password into a Notepad window, they were gathered in the screenshots. “Similarly, when I filled out a loan application PDF in Microsoft Edge, entering a social security number, name and DOB, Recall captured that,” Avram Piltch writes . The tool, however, didn’t record details when they were entered on a couple of online stores. Most Popular By Nena Farrell Microsoft pointed to its product information that says the system will get better over time and that people should report if sensitive information is captured by Recall. While that may be the case, it’s unlikely that any system can correctly determine what is and isn’t sensitive every time. And that could make it a bigger target for hackers. For years, North Korean nationals posing as tech workers have tried to get hired by global businesses so they can send their wages back to help the Hermit Kingdom pay for its nuclear programs. Increasingly, some companies are revealing they were targeted, and investigators are unravelling the schemes. This week, the US government indicted 14 North Koreans for their alleged role in generating $88 million , stealing sensitive business information, and attempting to use that information to extort more payments from companies. To get hired, the FBI alleges, the IT workers stole real identities, paid people in the US to use their home Wi-Fi connections, or paid them to attend job interviews. Researchers from Google-owned cybersecurity firm Mandiant who focus on North Korea say that in recent months they’ve seen IT workers following through on leaking sensitive data and demanding more cryptocurrency than ever before—although, they say this desperation could be a sign of the schemes becoming less effective. File-sharing software firm Cleo this week warned customers to implement a new security patch to prevent a wave of intrusions by cybercriminals actively exploiting a vulnerability in its code. Researchers at security firm Huntress Labs told news outlet Recorded Future that at least two dozen organizations have already been breached by the hackers exploiting the Cleo flaw. Huntress has found a sample of malware found on those victims’ networks it calls Malichus, and says it appears to have been used by a sophisticated hacker group. Huntress also noted that Blue Yonder, a software firm breached by the Termite ransomware gang in November, had a vulnerable instance of Cleo’s software exposed on its network, and some evidence suggests the same cybercrime group may now be using the software’s vulnerability to hit other victims. Cleo first released a patch for the bug currently being exploited in October, but hackers appear to have circumvented it, and the company is urging customers to apply its new patch now.
Huntress Frequently Asked Questions (FAQ)
When was Huntress founded?
Huntress was founded in 2015.
Where is Huntress's headquarters?
Huntress's headquarters is located at 6996 Columbia Gateway Drive, Ellicott City.
What is Huntress's latest funding round?
Huntress's latest funding round is Series D.
How much did Huntress raise?
Huntress raised a total of $308.05M.
Who are the investors of Huntress?
Investors of Huntress include Sapphire Ventures, Meritech Capital Partners, Kleiner Perkins, ForgePoint Capital, JMI Equity and 8 more.
Who are Huntress's competitors?
Competitors of Huntress include ActZero and 8 more.
Loading...
Compare Huntress to Competitors

Proofpoint is a cybersecurity company that provides human-centric security solutions across various sectors. The company offers products and services to protect against cyber threats, safeguard sensitive information, and ensure compliance with regulatory requirements. Proofpoint's solutions include threat detection, data loss prevention, insider threat management, security awareness training, and email security, serving diverse industries such as federal government, healthcare, financial services, and higher education. It was founded in 2002 and is based in Sunnyvale, California.

CyCraft is a cybersecurity company that specializes in automated threat investigation and incident response solutions. The company offers a platform that integrates endpoint detection and response, account attack path analysis, and external attack surface management to provide cybersecurity solutions. CyCraft primarily serves enterprise customers in the financial services industry, high-tech manufacturing, and government agencies. It was founded in 2017 and is based in New Taipei City, Taiwan.
PhishCloud provides IT security services focusing on anti-phishing solutions. The company offers a platform named PHISH360° that includes management of malicious links and training for employees. PhishCloud's services aim to protect businesses from phishing attacks across digital platforms such as email, social media, and messaging applications. It was founded in 2018 and is based in Seattle, Washington.

Judy Security focuses on providing cybersecurity solutions for managed service providers (MSPs) and managed security service providers (MSSPs), focusing on the needs of small and medium-sized businesses (SMBs). The company offers artificial intelligence (AI)-driven, enterprise-grade security platforms including endpoint resiliency, identity access management, compliance automation, and threat detection and response. Judy Security's products are tailored to support businesses in safeguarding their digital assets and ensuring regulatory compliance. Judy Security was formerly known as AaDya Security. It was founded in 2019 and is based in Detroit, Michigan.
ASecureLife focuses on providing security solutions and smart home technology. It offers a range of services, including home security systems, smart home devices, personal safety equipment, online security services, and financial security services. It primarily caters to individuals seeking to enhance the security of their homes and personal information. It was founded in 2008 and is based in Salt Lake City, Utah.

Cybereason specializes in cybersecurity solutions. It facilitates threat detection and response, ransomware protection, and proactive threat hunting, all designed to provide comprehensive protection against cyber attacks. Its primary customers are businesses and organizations across various sectors that require cybersecurity measures. It was founded in 2012 and is based in La Jolla, California.
Loading...